Blog


Post Quantum Scam

Jump the Q
Post Quantum Validation

Post Quantum Resource
Post Quantum Public Education
Post Quantum Regulation

Post Quantum Continuity
Post Quantum Threat Surveillance
Post Quantum R&D

Post Quantum Migration
Post-Quantum Digital Signing for PDF Documents

Mind Your P's and Q's
A comic series by pQCee all about Quantum: Mind your P's and Q's.
Enabling a Smooth Migration Towards Post-Quantum Security for Ethereum

Quantum Computing for Beginners
Discover and learn about Quantum Computing in 5 minutes!
Towards Discovering Quantum-Threats for Applications Using Open-Source Libraries
Quantum-Safe Message Authentication for Industrial IOT using “QKDLite” with LPN
Post-Quantum Adversarial Modeling: A User’s Perspective

The Quantum Dilemma

Quantum Annoyance: The Simple Answer Against Store-Now-Decrypt-Later Attacks
Quantum Annoyance
Migrating Blockchains Away from ECDSA for Post-Quantum Security: A Study of Impact on Users and Applications
Due to the potential threat from quantum computers, these blockchain implementations need to migrate away from ECDSA to a post-quantum algorithm before quantum computers become powerful enough.

Are we ready to start Quantum-readiness migration
Calibrating Learning Parity with Noise Authentication for Low-Resource Devices
LPN setup is complicated by different parameter choices, including key length, noise rate, sample size, and verification window, which can determine the usability and security of the implementation.
Software will save the Quantum world (part 2)

Software will save the Quantum world (part 1)

Is Post-Quantum readiness another Y2K
ZKBdf: A ZKBoo-based Quantum-Secure Verifiable Delay Function with Prover-Secret

Quantum readiness, here we come

Time to upgrade your encryption

How will going paperless change our trust model

Why digital signatures
Quantum Computing Threat Modelling on a Generic CPS Setup
What is an appropriate threat modelling method to understand your enterprise’s exposure to quantum threats? We recommend Process for Attack Simulation and Threat Analysis (PASTA).

What is Cryptography
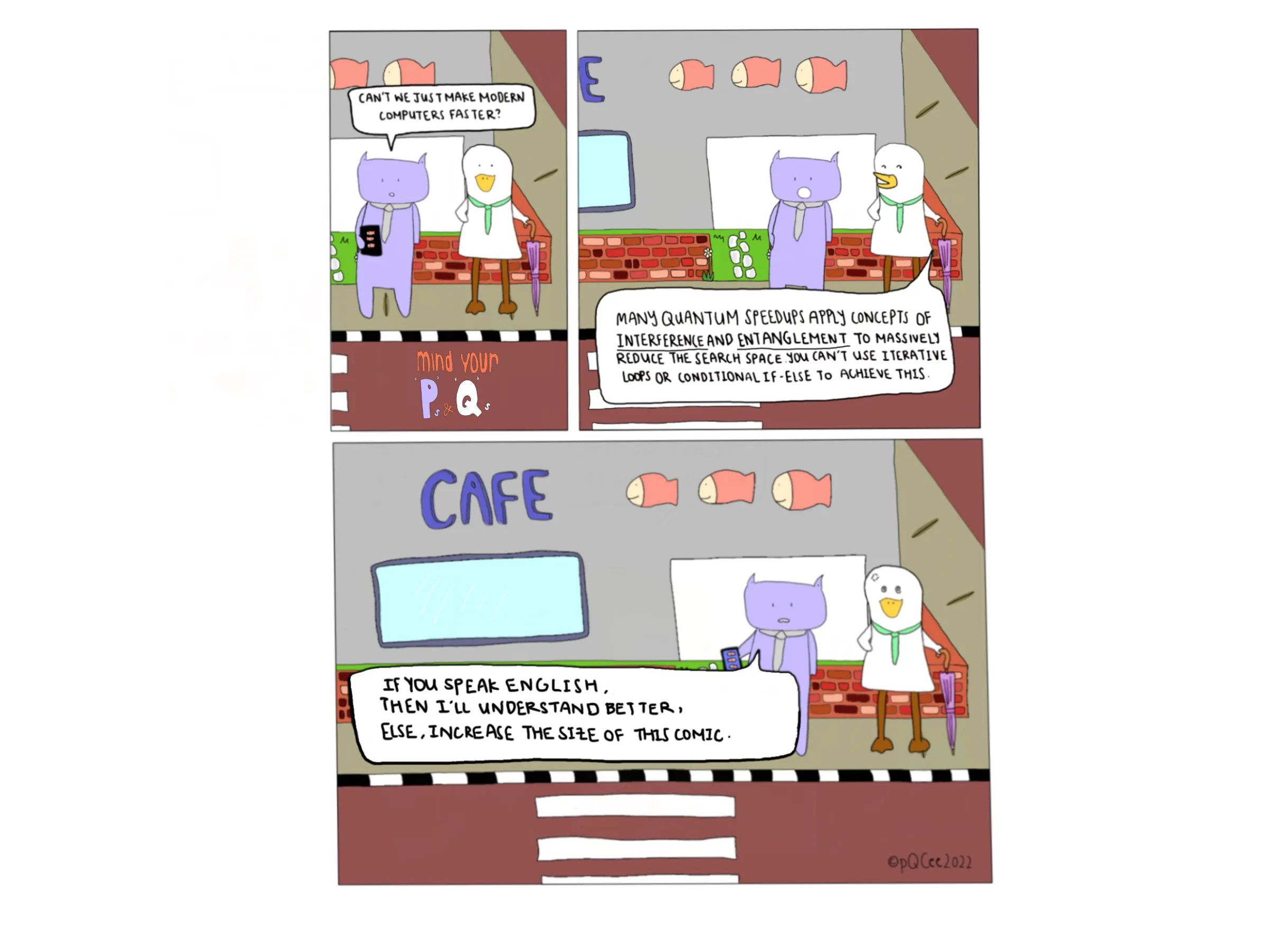
How do Quantum computers out-perform modern computers
Layering Quantum-Resistance into Classical Digital Signature Algorithms
Is it possible to make ECDSA signatures quantum-secure? Yes.

What is Post Quantum

What are Quantum Computers
Challenges of Post-Quantum Digital Signing in Real-World Applications: A Survey
In this paper, we study the use of digital signatures in 14 real-world applications across the financial, critical infrastructure, Internet, and enterprise sectors.