February 23, 2025
Quantum Computing
Quantum computing represents a new computational paradigm to perform certain classes of computing tasks significantly faster than classical computers. Data in quantum computing is represented in qubits (or quantum bits) which enables quantum computers to operate and evaluate all possible solutions simultaneously, whereas classical computers evaluate one solution at a time sequentially. The two properties that qubits exhibit to enable this speedup are (i) Superposition, where the state of each qubit is transient and exists between the values of 0 and 1 simultaneously; and (ii) Entanglement, where the states of multiple qubits correlate with one another such that changing the state in one of the qubits will cause a relative change in the other qubits instantaneously.
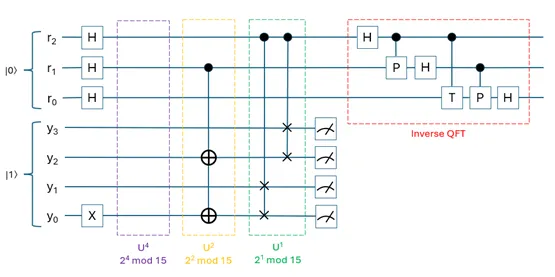
A quantum program (or quantum circuit) applies a specific sequence of quantum gates to manipulate the state of the qubits and causes interference in qubit states to amplify probabilities of correct solutions and diminish likelihood of wrong solutions. Some programs, such as Shor’s Algorithm shown in Figure 1 below, require the execution to be repeated multiple times for a higher likelihood to get the correct solution.
A physical qubit (or noisy qubit) is a hardware implementation of a qubit and is prone to data corruption from random errors (known as noise) introduced by its environment. Quantum error correction techniques can be used to group multiple noisy qubits together to build a logical qubit (error-free qubit). The duration in which a qubit can remain error-free is referred to as its coherence time, in which qubits with longer coherence can support more gate operations and more classes of algorithms. Manufacturers of quantum computers work towards increasing the number of qubits available in the quantum computer, decreasing the error-rates in the qubits, and increasing the coherence time of the qubits. Current quantum computers are typically made up of hundreds or thousands of noisy qubits and categorised as Noisy Intermediate-Scale Quantum (NISQ) computers. The goal is to build quantum computers with thousands of logical qubits and usher in the Fault-tolerant Quantum Computing (FTQC) era where quantum computers will be routinely used to perform tasks which are not feasible even using the most powerful classical supercomputers today.
The cryptanalytically relevant quantum computer (CRQC) is defined as a quantum computer sufficiently powerful to compromise existing cryptographic systems, such as public key encryption and digital signature schemes. Based on current cryptographic key sizes, it is estimated that a CRQC will be a quantum computer with at least 2,000-4,000 logical qubits. Cybersecurity threats such as identity spoofing, transaction tampering and information disclosure will become commonplace unless proper quantum-safe migration steps are taken prior to the existence of a CRQC. The primary quantum threat that is best understood is the harvesting attack or the “store-now-decrypt-later" attack. In this attack, attackers will first harvest existing data that is protected using classical cryptography. This data is stored until the availability of the CRQC in the future where the attacker will then use Shor’s algorithm to decrypt the harvested data to reveal its contents. The National Institute of Standards and Technology (NIST) has standardised and published a set of post-quantum cryptographic (PQC) algorithms, designed to be safe from both classical and quantum attacks, to mitigate against the quantum threat on existing security systems.
Apart of quantum computing, another technology field of interest is quantum communications which exploits the quantum photonic properties of light. Two use-cases of quantum communication that are being tested by the industry are (i) Quantum random number generator (QRNG) which uses the superposition property of photons to obtain unpredictable and indeterministic random numbers which can be used as inputs for secret key generation and for fair sampling; and (ii) Quantum key distribution (QKD) which builds on QRNG with eavesdropping detection to distribute shared secrets between two communicating parties. Different organisations are planning to use combinations of PQC, QRNG and/or QKD as strategies to secure organisational data and IT communications infrastructure.